As you may recall at the time that the kfd exploit emerged for iOS & iPadOS 16.0-16.6 beta 1, conversations immediately popped up regarding whether or not it could be used for a jailbreak. Following conversations by high-profile members of the jailbreak community, including Dopamine lead developer Lars Fröder (@opa334dev), it became apparent that we would still need a PPL bypass for there to be any hope of a jailbreak.

For those unaware, PPL stands for Page Protection Layer, and it is one of several security mitigations that prevents attackers from assuming control over the kernel memory of your iPhone or iPad. More specifically, it prevents user space code from being modified once code signature verification is finalized, ensuring that all code on your device is doing what it supposed to do, and nothing it’s not supposed to do.
Interestingly enough, there is a security change in iOS & iPadOS 17 that appears to be turning quite a few heads, including Fröder’s. Dubbed CVE-2023-41981, this issue is logged as a Kernel issue in Apple’s “About the security content of iOS 17 and iPadOS 17” web page for iOS 17, and according to the description, “an attacker that has already achieved kernel code execution may be able to bypass kernel memory mitigations.”
So what does this mean? One may only need to read one of Fröder’s replies to a post shared on X this week to find out:
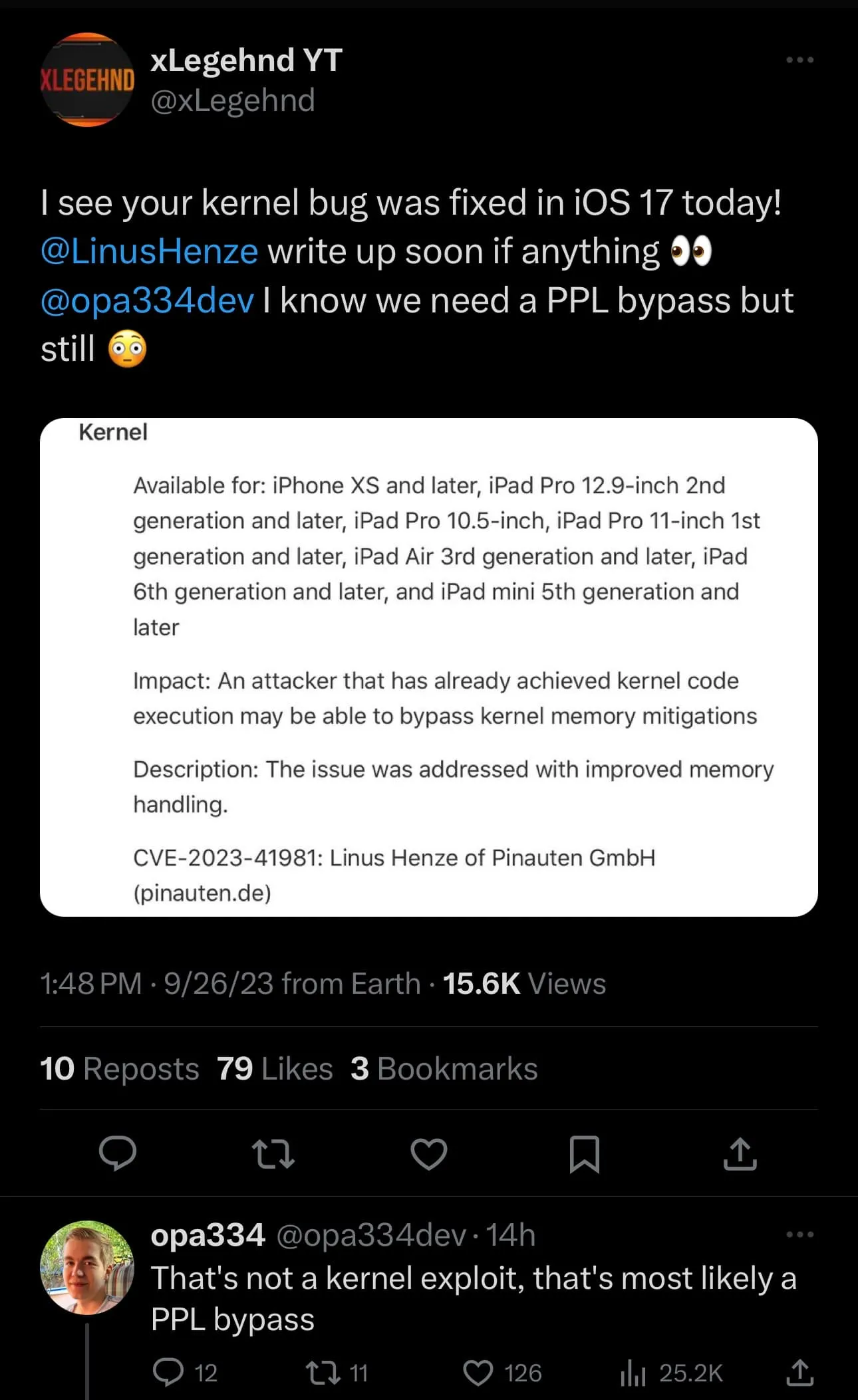
As it would seem, this may actually be a PPL bypass — the final piece of the puzzle that may be required to complete an iOS & iPadOS 16 jailbreak for newer devices up to and including the iPhone 14 Pro Max (iPhone 15 series are excluded because they can’t run iOS 16 since they ship with iOS 17).
Furthermore, the person who appears to have reported this issue to Apple is none other than famed security researcher Linus Henze of Pinauten GmbH, the same talented lad that brought us the Fugu15 developer jailbreak that laid the framework for the Dopamine public jailbreak on iOS & iPadOS 15.0-15.4.1.
If it seems like the stars are already aligning, try to keep in mind that it remains unconfirmed at the time of this writing whether this is actually a PPL bypass or not. In addition, Henze has yet to produce a writeup, so it remains to be seen if those efforts will go on to help the jailbreak community live on a little longer.
It’s also worth noting that Henze isn’t obligated to produce a write-up. So even if this is an iOS 16-viable PPL bypass, whether or not it sees the light in one form or another remains to be seen.
If anything else, it’s worth keeping your eye on if you’re waiting for an iOS & iPadOS 16 jailbreak. After all, now that iOS & iPadOS 17 are out, this is the time when security researchers will start dumping their iOS & iPadOS 16 research and move on to exploiting Apple’s latest firmware.


