Researchers have discovered “Gmera Trojan Mac”, a trojan targeting crypto dealers using Apple Macs. Malware infects users by imitating authoritative websites with a similar domain and user interface to trick unwary users into visiting them.
According to ESET, researchers at cybersecurity company ESET have discovered malware that can steal data using “browser cookies, crypto wallets, and screenshots.”
What is the Gmera Trojan for Mac and how does it work?
GMERA is malicious malware masquerading as Stockfolio, a legal trading tool for Apple Mac users. According to research, there are two varieties of this malware, one of which has been identified as a Trojan. The former is known as MacOS.GMERA.A and the latter is known as Trojan. macOS.GMERA.B.
Cybercriminals often use GMERA to steal data and upload it to a website they control. Remove GMERA as soon as possible to avoid any damage caused by this infection.
Types
Trojan.MacOS.MERA.A
The Gmer Mac Trojan is a fictional character. macOS.MERA. User information such as usernames, IP addresses, applications in the Applications folder, and files in the /Documents and /Desktop directories are collected in the sample.
- It also captures OS installation date, graphics, and displays information, wireless information, and screenshots.
- It sends information to a server run by cybercriminals.
- The stolen data/details may contain sensitive information used to make money in various ways.
- Obtaining personal information can lead to privacy breaches, identity theft, financial loss, and other issues.
Trojan.MacOS.GMERA.B
The Trojan.MacOS.GMERA.B (Gmera Trojan Mac) variant collects information such as the victim’s username and IP address, as well as a number of other files.
- One serves as a “persistence mechanism”, allowing GMERA to continue running even after a system restart, reboot, logout, etc.
- Once launched, software like GMERA hides behind the actual Stockfolio trading app and runs in the background.
- Take immediate action to get rid of the infection.
Working
Gmera Trojan Mac operators imitate legitimate websites to distribute malware. These websites are strikingly identical and seem genuine to the untrained eye.
Although the researchers had no idea where the malware was spreading, Kattana warned users about a malicious impersonation service luring them into downloading the Trojan.
However, the researchers were unable to link the campaign to the GMERA malware. According to the researchers, the infection was also spread through Trojans.
Symptoms
Trojans are designed to infiltrate the victim’s computer and go unnoticed unnoticed, so there are no obvious signs on the infected PC. Infected email attachments, fraudulent web marketing, social engineering, and software hacks are malicious variants of legitimate Stockfolio applications.
Source of infection
In their latest attacks, it was discovered that the developers of the GMERA virus used a malicious version of the real bitcoin trading application Kattana.
- The creators of the GMERA malware turned the current Kattana into malware.
- They also developed web pages for cryptocurrency trading malware for Apple Mac users.
- Most likely, the operators personally contacted their intended victims and convinced them to install malware.
- Browser cookies, browsing history and cryptocurrency wallet passwords were stolen using reverse shells.
Steps to Remove Gmera Mac Trojan
1. Remove files and folders associated with Gmera Mac trojan
- Click the Finder icon in the Menu bar. Select “Go”and then “Go to folder…”.
- Look for suspicious and untrusted files created by malware in the /Library/LaunchAgents folder.
- Find all recently downloaded files in the Launch Agent folder and move them to the Trash folder.
- “myppes.download.plist”, “mykotlerino.Itvbit.plist”, “installmac.AppRemoval.plist”, “kuklorest.update.plist”, etc. are some examples of files created by a browser hijacker or adware.
- Detection and removal of adware files in the “/Library/Application”support folder.
- Enter “/Library/Application Support”in the “Go To Folder…”panel.
- Look for any suspicious recently added directories in the Application Support folder.
- If you find any of them, such as “NicePlayer”or “MPlayerX”, move them to the Trash folder.
- Look in the /Library/LaunchAgent folder for files created by malware.
- If you find any suspicious files, you should find them and move them to the Trash folder.
- Look in the /Library/LaunchDaemons folder for files created by malware.
- In the Browse to folder field, enter /Library/LaunchDaemons.
- Search the newly opened “LaunchDaemons”folder for any suspicious files that have been recently added and move them to the “Trash”folder.
2. Remove Gmera from internet browsers
Remove dubious and malicious extensions from Safari.
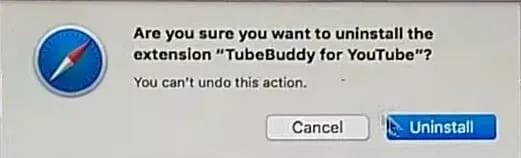
- Open the “Safari”browser from the “Menu Bar”. Select “Safari”and then “Settings”from the drop-down menu.
- Select the “Extensions”you recently installed in the Settings window that opens.
- All of these extensions should be recognized and you should click on the “Uninstall”button next to them to remove them. If you are still unsure, you can remove all extensions from the Safari browser because none of them are required for the browser to work properly.
- You can reset Safari browser settings if you continue to receive unwanted web page redirects or intrusive ads.
Reset Safari
- Choose “Preferences”from the Safari menu.
- Set the extension to “Off”on the Extension tab. Installed extensions in Safari are disabled as a result of this setting.
- Select the General tab from the Settings menu. Replace the default home page with your desired URL.
- Examine the default provider settings for search engines. Select the “Search”tab in the “Settings”field and the desired search engine, such as “Google”.
Clear cache in Safari browser
- Select the “Advanced”tab and “Show Develop Menu in Menu Bar”in the “Settings”box.
- Select Clear Caches from the Develop menu.
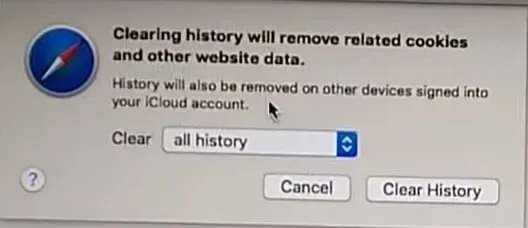
- Clear your browsing history and website data. Select “Clear History and Website Data”from the “Safari”menu.
- After that select “all history”and then “Clear history”.
Mozilla Firefox: Removing Unwanted and Malicious Plugins
- Gmera add-ons must be removed from Mozilla Firefox.
- Launch the Mozilla Firefox web browser. In the upper right corner of the screen, click the “Open Menu”button.
- Select Add-ons from the menu that opens.
- Select “Extension”from the drop-down menu to see a list of all recently installed add-ons.
- Select all questionable add-ons and click the “Uninstall”button next to them to remove them.
Reset Mozilla Firefox preferences
If you want to “reload”the Mozilla Firefox browser, follow the instructions below.
- Open the Firefox Mozilla browser and go to the top left corner of the screen to the “Firefox”button.
- Select “Troubleshooting Information”from the “Help”submenu in the new menu.
- Click the Reset Firefox button on the Troubleshooting Information screen.
- By selecting the “Reset Firefox”option, you confirm that you want to reset Mozilla Firefox settings to factory defaults. The browser will restart and the settings will be reset to factory settings.
Google Chrome: Removing Unwanted and Malicious Extensions
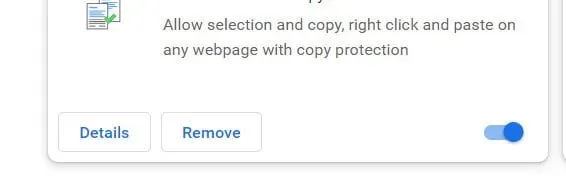
- Open the Chrome browser and select “Chrome Menu”from the drop-down menu. Select “More Tools”and then “Extensions”from the menu.
- Find all recently installed add-ons and extensions under the Extensions tab.
- Select “Cart”from the drop-down menu. Any third-party plugin is not essential for the smooth operation of the browser.
Reset Google Chrome
- Open your browser, go to the top right corner of the window and click on the three line bar.
- Select “Show advanced settings”at the bottom of the window that opens.
- Scroll to the bottom of the window you just created and select Reset Browser Settings.
- In the Reset Browser Settings window that opens, click the Reset button.
3. Delete or remove the infected file
The Trojan came through a file you downloaded or an application or extension you installed from an untrusted source. It’s entirely possible that a simple removal could fix the problem, but that’s far from the case given how difficult it is to kill malware.
Use LaunchPad on Mac
- The Launchpad can be opened by clicking it in the Dock or by opening it from the Applications folder.
- You can also pinch the trackpad with your thumb and three fingers.
- If the application is not documented in Launchpad, enter its name in the search bar. Swipe right or left on the trackpad with two fingers to open the next or previous page.
- Press and hold any app until it starts to wiggle while holding down the Option key.
- Next to the app you want to uninstall, click the Uninstall button, then confirm by clicking Uninstall.
- The software is immediately removed. Apps not shown weren’t downloaded from the App Store or are required by your Mac.
- To remove an app that was not obtained from the App Store, use the Finder instead of the App Store.
To remove an application, use the Finder.
- Find the app in the Finder. The bulk of the applications reside in the Applications folder, which can be accessed by selecting Applications from the sidebar of any Finder window.
- You can also use Spotlight to search for software. Hold down the Command () key and double-click it in Spotlight.
- Select an app and drag it to the Trash using File > Move to Trash.
- The Recycle Bin appears in the macOS Dock.
- Use the administrator account name and password on the Mac if a username and password is required. This is most likely the username and password you use to log in to your Mac.
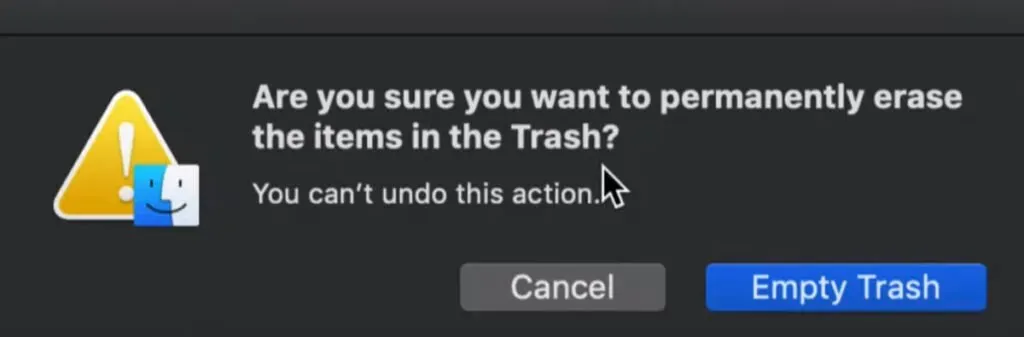
- To get rid of the software, go to Finder > Empty Trash.
4. Download a Time Machine backup
Trying to figure out if your Mac has a Trojan and then manually removing it is likely to be a daunting task. It may be easier to simply restore a Time Machine backup before installing the infected file.
- To restore your Mac from a Time Machine backup, follow these steps:
- Select the Time Machine icon from the menu bar.
- Enter the “Time Machine”option.
- A stack of Finder windows will appear, each representing a different backup.
- Click the “Restore”button after selecting what you want to restore.
5. Use antivirus software
You should run a virus scan whenever you suspect that your Mac is infected with malware. This includes if you suspect you are infected with a Trojan. Antivirus software checks files for dangerous code.
Look for browser add-ons.
Scan your computer for browser hijackers and ad extensions:
- Choose Safari > Preferences from the menu bar. Check the existing home page URL and make any necessary changes.
- Then go to the “Extensions”tab and remove anything that is unfamiliar to you, as they can spy on you, save your personal information and redirect you to malicious websites.
Remove all questionable apps from your device.
- Check if you have unfamiliar software installed:
- Navigate to the Applications folder in the Finder by choosing Go > Applications or by pressing Shift + Command + A.
- Remove all unrecognized apps from the list by scrolling through it.
- Then empty the trash.
Remove all questionable login items from your system.
- Remove any login items that are acting weird as part of your “Mac malware removal”goal.
- Some of them may be unfamiliar to you, or you may not remember turning them on.
- To prevent certain items from running at startup, follow these steps: Uncheck the options in Apple menu > System Preferences > Users & Groups > Login Items.
On Apple macOS, create a new profile.
You can remedy the situation by creating a new profile in macOS if the Mac virus is targeting the user and not the device. To create a new user profile, follow these steps:
- Go to System Preferences > Users & Groups from the Apple menu.
- To make changes, unlock the page.
- Select the type of person you want to add by clicking the + button (Administrator or Standard).
- Create a new user by entering a new username and password and clicking “Create User”.
6. Factory Reset Your Mac
This is the last resort, but if nothing else helps to remove the Trojan from your Mac, you can also perform a factory reset. This will reset your Mac to factory settings, deleting everything from it, including all your data, so make a backup beforehand. You will need to enter recovery mode to get started.
Here is how to enter recovery mode on M1 Mac:
- Turn off your Mac.
- Now press and hold the Power button for a few seconds.
- Hold down the button until you see Loading launch options.
- Continue by pressing the Enter key.
- Enter the administrator password when prompted.
- Now go to Disk Utility and look for the “Erase”option to remove all files from Mac.
Conclusion
Gmera is also known as the Kassi Trojan, a dangerous computer infection that masquerades as Stockfolio, a genuine and useful trading tool for Mac users. To remove “Gmera Trojan Mac”and clean your computer from malware, use all of the above procedures.
FAQ
Can trojans affect a Mac?
If your Mac is infected with a Trojan horse, the program can do everything from installing other viruses or spyware to giving a hacker complete remote control over your system. A Trojan horse is terrible news for both you and your machine.
How to know if your Mac has a Trojan virus?
Your Mac starts behaving strangely and doing things you don’t expect. Your Mac starts to run slowly, as if something is using all the CPU resources. Ads start appearing on your PC.
How can malware be hidden?
Malware can remain an Advanced Persistent Threat (APT) using polymorphism, encryption, and in-process execution. Each time a polymorphic code is played, it changes. By changing the encryption/decryption keys on each new device, encryption hides these activities and keeps them in view.
What is a Trojan? Is it a virus or malware?
A Trojan horse is a kind of malware that disguises itself as a real program and is downloaded to a computer. An attacker often uses social engineering to inject malicious code into genuine applications in order to gain access to the system using their program.