Today is the day many avid jailbreakers have been waiting for. Security researcher Linus Henze gave a highly anticipated keynote at the Objective by the Sea security conference, during which he demonstrated his Fugu15 jailbreak on an iOS 15.4.1 device using a fun Safari-based JailbreakMe method.
Installation via Safari
In the demo video, Henze navigates https://jbme.pinauten.de/to the standard Safari web browser on the iPhone and clicks on a hot link on a web page to initiate the installation of the Fugu15 app on the home screen:
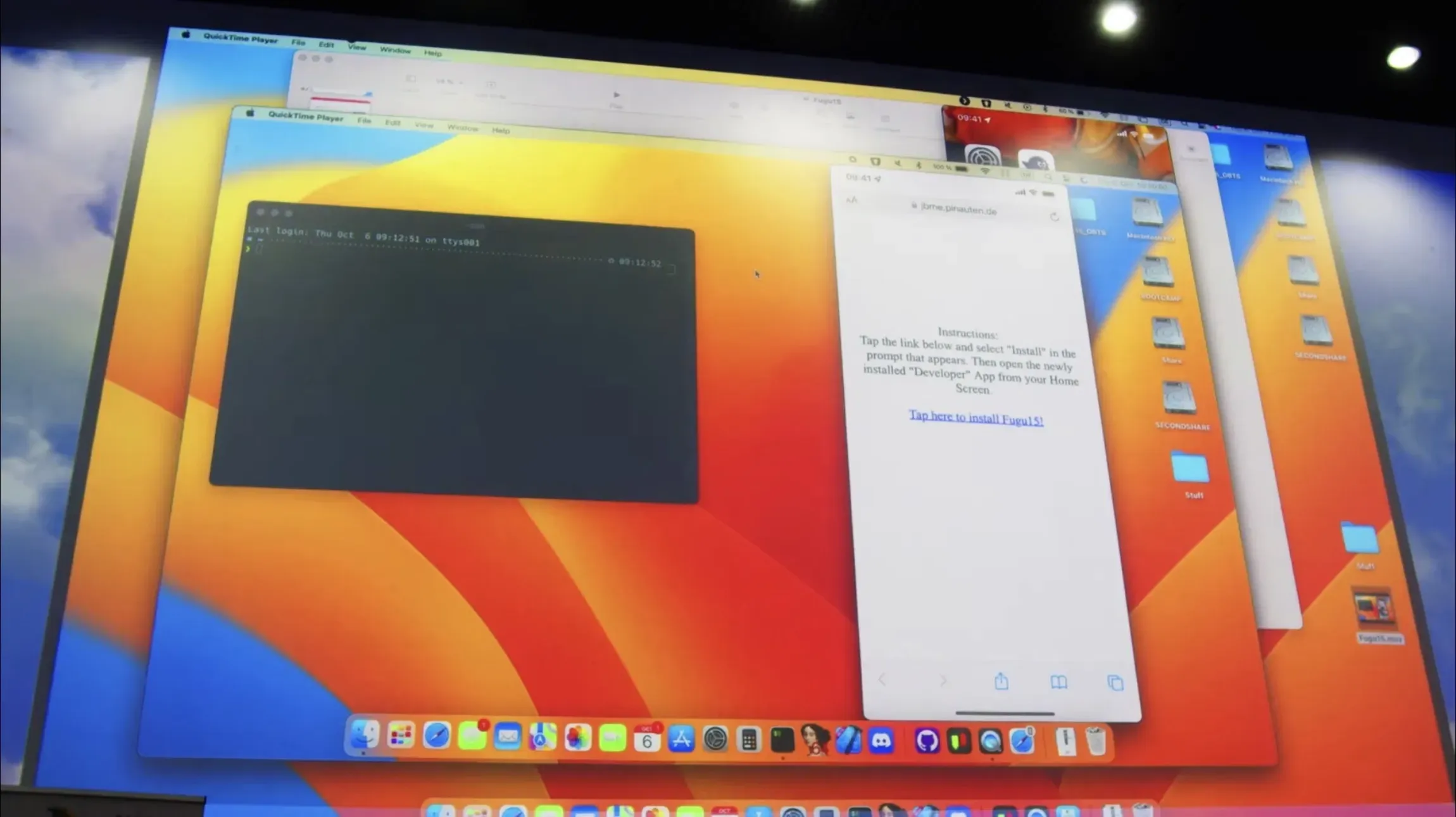
After Henze confirms the installation in the iOS pop-up window, the Fugu15 app will load on the home screen in the same way as the app from the App Store. When completed, the app icon looks just like the Apple Developer app, not the Fugu15 app:
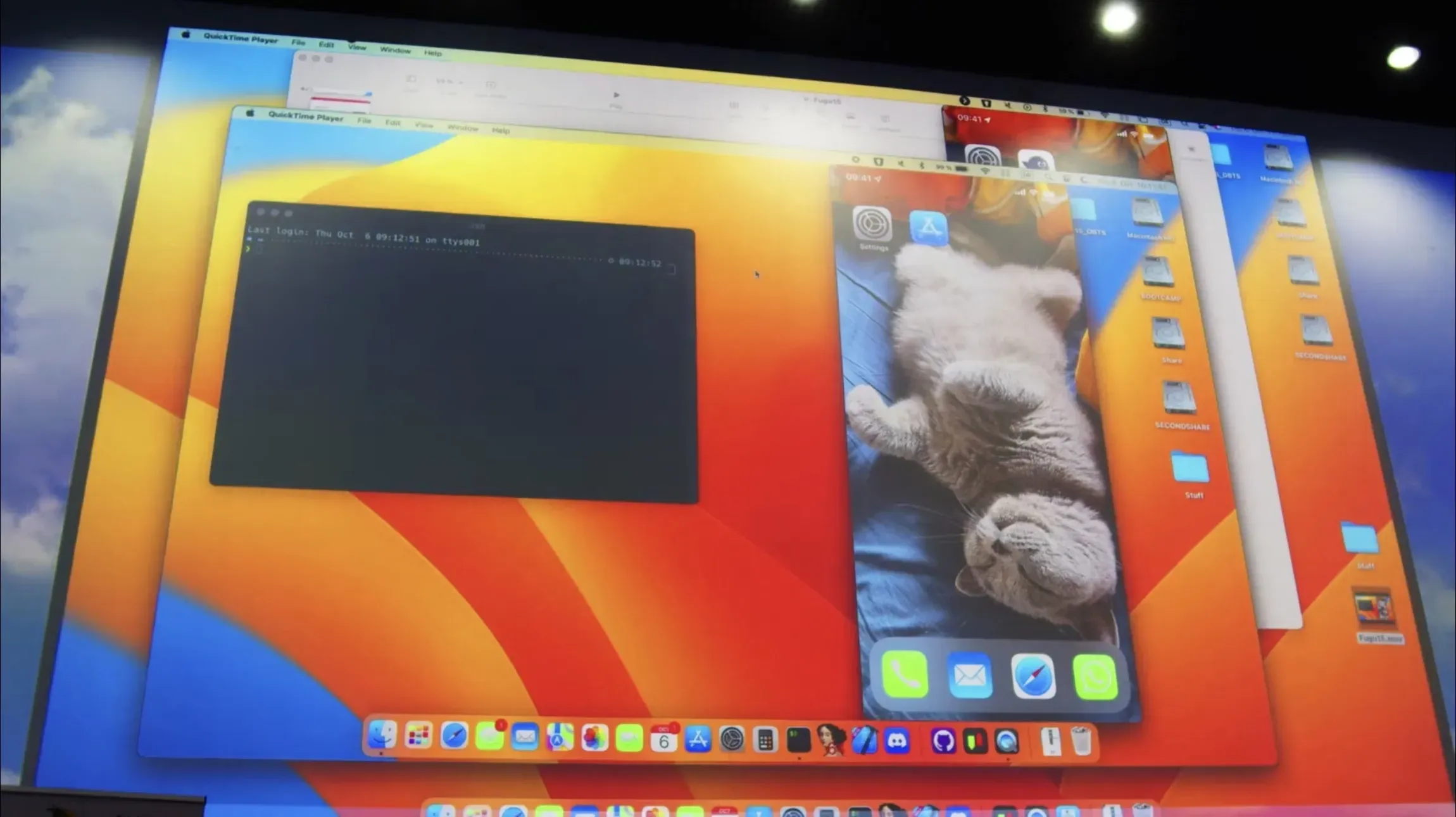
Henze explains that the reason the Apple Developer app appears on the home screen is because he needs a truly signed app in order to download Fugu15 on the device. Once this is complete, Fugu15 can be injected into the app, which happens almost immediately after Henze launches the newly downloaded Apple Developer app:
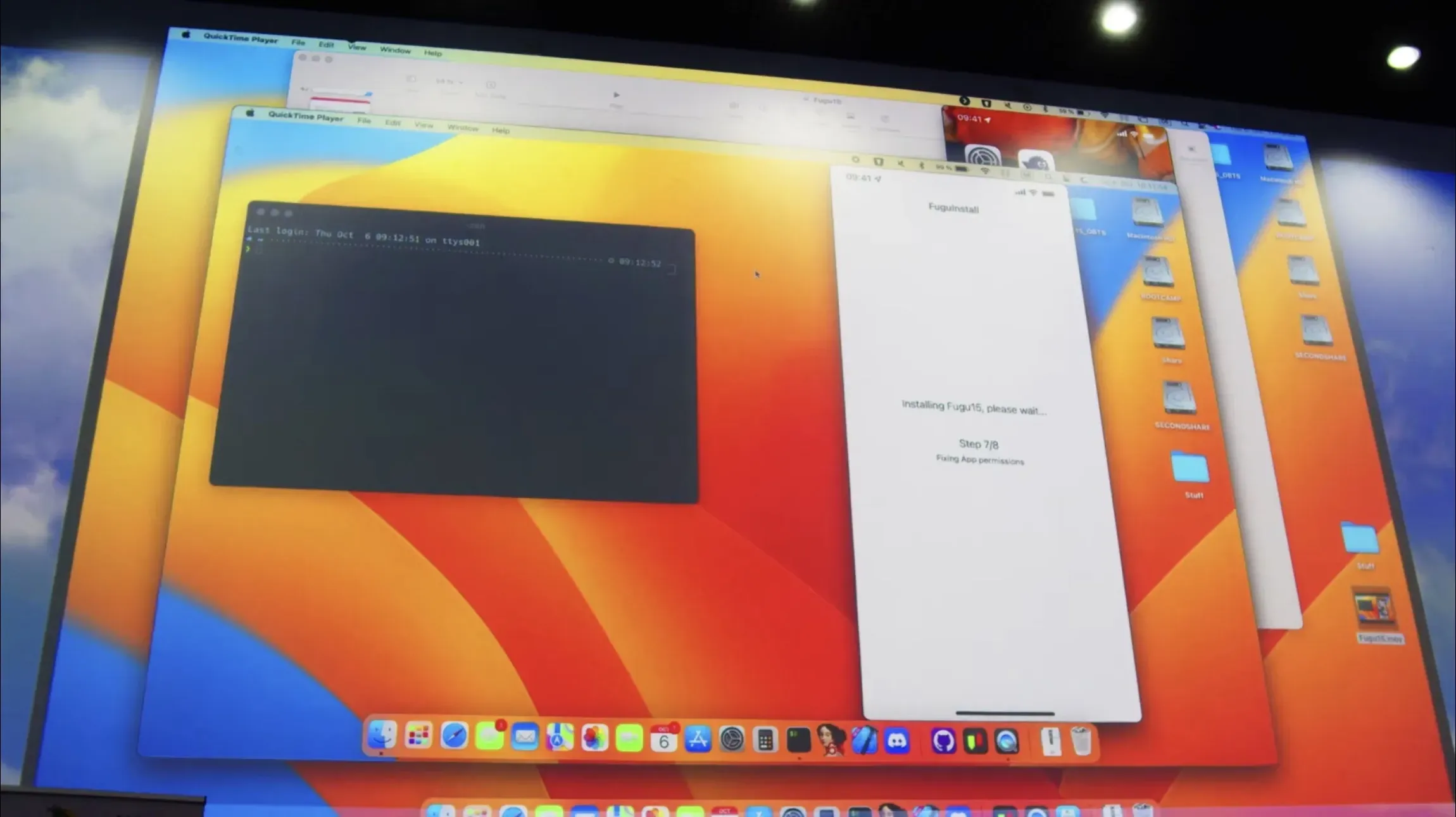
After a short wait, the app prompts Henze to uninstall the Developer app, which he does, leaving the Fugu15 jailbreak app behind.
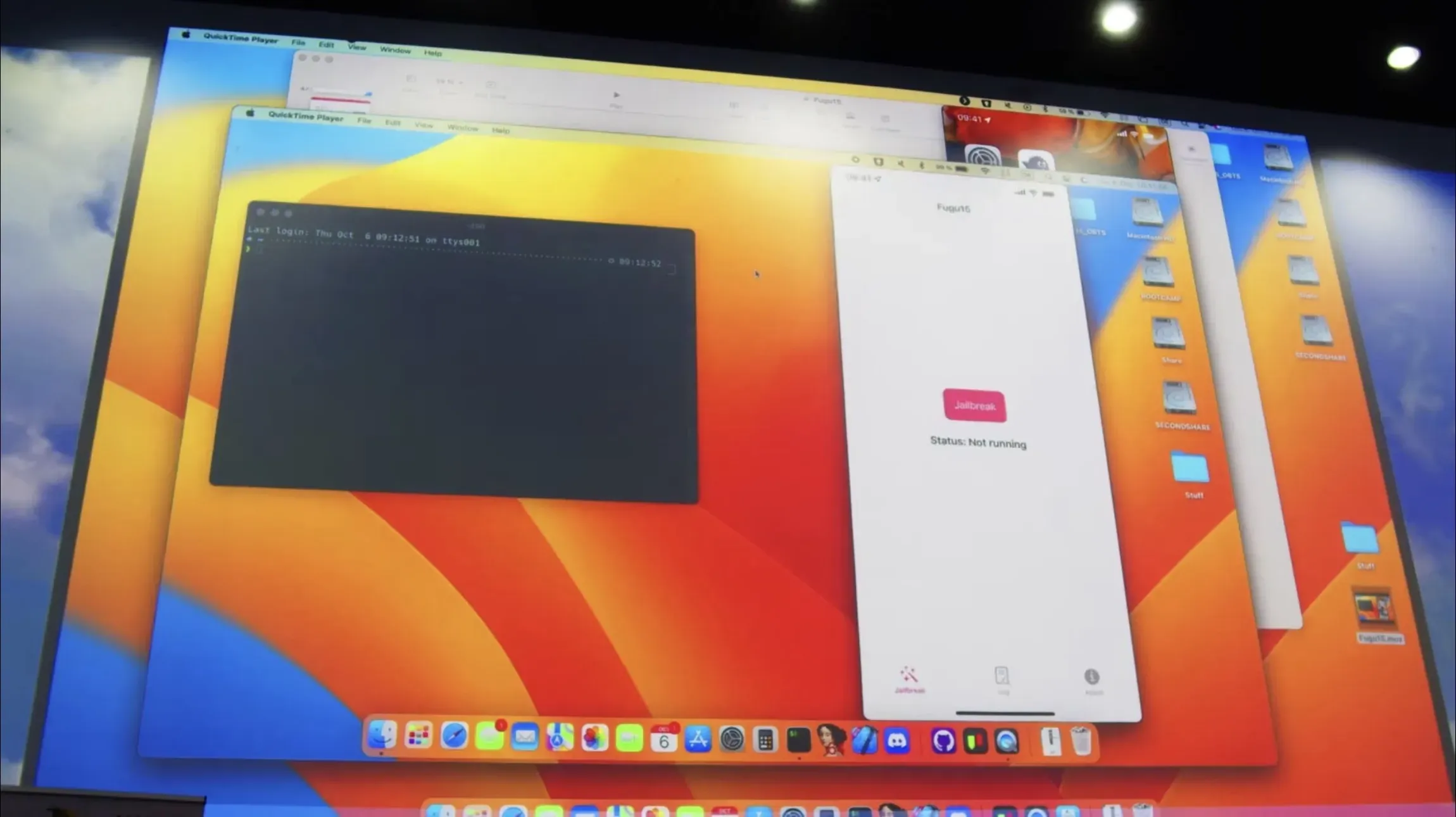
Pressing the jailbreak button
In the Fugu15 app, we see a lone jailbreak button that Henze happily presses:
After the jailbreak process is complete, Henze switches to the log to showcase everything that just happened, then navigates to the terminal on his Mac to install the Procursus bootloader.
Sileo and Prokurs on Fugu15
Indeed, Fugu15 installs the same Procursus bootloader used by the Odyssey team in their Odyssey, Taurine and Cheyote jailbreaks, which means the Sileo package manager (not Cydia) will be installed on the device:
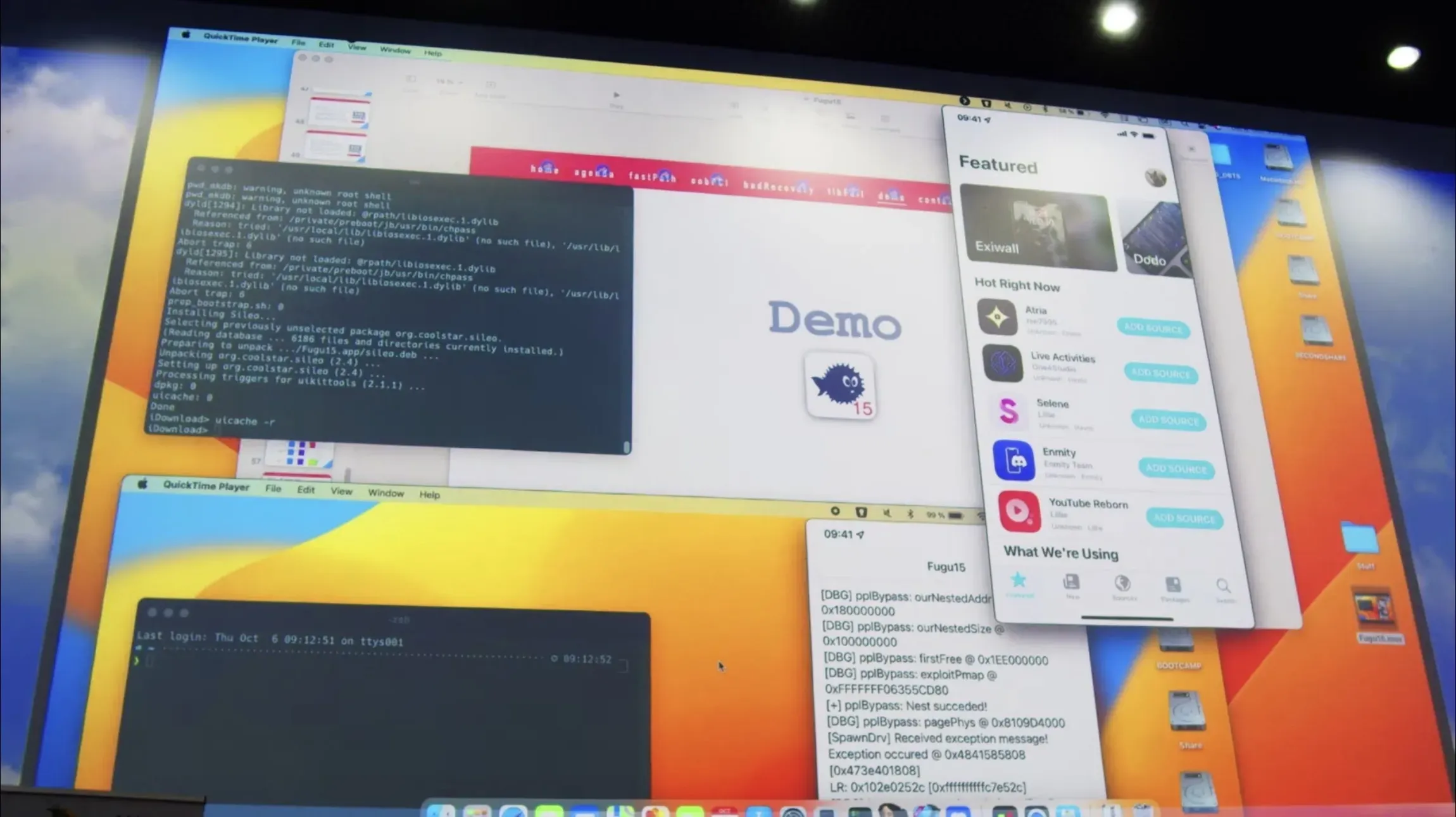
Towards the end of the demo, Henze introduces us to Sileo, explaining that there are currently no jailbreak tweaks to install because his Fugu15 jailbreak is unrooted and the jailbreak tweaks have not yet been updated for compatibility. This warning echoes the same tone expressed by lead Odyssey developer Team CoolStar, who has yet to release the Cheyote publicly for the same reason.
Henze’s Fugu15 jailbreak project depends on a CoreTrust bug to sign the Fugu15 jailbreak app and bypass Apple Mobile File Integrity (AMFI). It also appears to be using a Page Protection Layer (PPL)/Pointer Authentication Code (PAC) bypass, as well as a bug that allows writes to PPL memory.
For now, Fugu15 has been shown to support A12-equipped devices and then works up to iOS 15.5 beta 4, including iPhone XS and later. Since most users are not on betas, this means that iOS 15.4.1 is the latest public iOS it supports. It is important to note that support for older devices such as the iPhone X and earlier models may be added in the future. Fugu15 is not untethered like Fugu14 is on unc0ver.
Watch live with Linus Henze
The full video stream of the Objective by the Sea security conference with Henze’s presentation is available on YouTube for those interested in watching it:
Since the Fugu15 release date is unknown at the time of this writing, it looks like the community will have to wait a little longer for the iOS 15.x jailbreak. But the demo was satisfying enough to make you feel like great things are on the way, whether you’re waiting for the Cheyote release for iOS 15.0-15.1.1 or the release of Fugu15 for iOS 15.0-15.4.1.
Were you impressed by the masterful Henze jailbreak demo on iOS 15.4.1? Let us know in the comments section below.


